
Monitor Critical IAM Actions in AWS Using AWS CloudTrail and Amazon Simple Notification Service
- Hendrik Hagen
- Aws
- April 15, 2025
Table of Contents
Introduction
In any cloud environment, identity and access management (IAM) is one of the most critical areas to secure. AWS IAM controls who can access your resources, what actions they can perform, and under what conditions. While it’s easy to focus on infrastructure protection like firewalls or encryption, overlooking IAM activity monitoring can leave serious gaps in your cloud security posture.
Monitoring events like user creation, deletion, and permission changes isn’t just about detecting malicious behavior — it’s also about catching accidental mistakes, maintaining compliance with security standards, and ensuring operational visibility. A compromised set of credentials or an overly permissive policy attached to a new user can lead to privilege escalation, unauthorized data access, or even complete account takeover.
By actively tracking IAM API calls through AWS CloudTrail and setting up real-time alerts for sensitive actions, you gain immediate awareness of changes within your environment. This allows your security teams to respond quickly, investigate unusual activity, and reduce the risk of breaches or misconfigurations before they cause damage.
In this post, we’ll look at how you can setup monitoring for IAM API calls by using CloudTrail in combination with Amazon EventBridge and AWS SNS.
Overall Architecture
Let’s begin by reviewing the demo infrastructure we’ll deploy as part of this blog post. The high-level diagram below outlines the key components involved in our setup. Our goal is to build a monitoring and notification pipeline for IAM API calls using CloudTrail, EventBridge, and SNS.
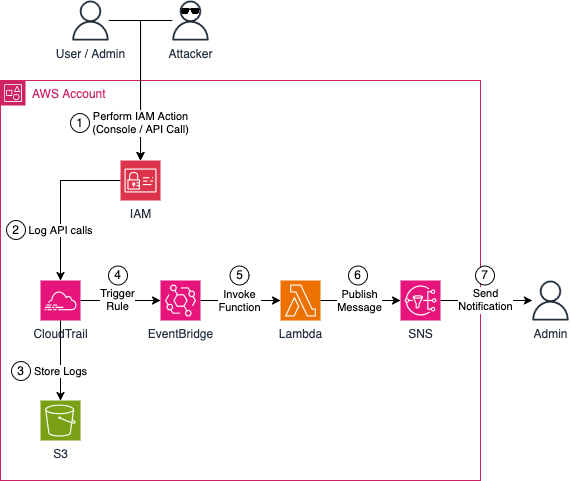
The infrastructure includes a CloudTrail trail, a logging S3 bucket, an EventBridge rule and trigger, a Lambda function, and an SNS topic for notifications. Here’s a step-by-step breakdown of how the workflow operates:
An IAM action is performed within the AWS account — this could be by a user, administrator, or potential attacker. The action might occur through the AWS Management Console or via programmatic API calls. Which specific actions to monitor can be defined during infrastructure setup.
CloudTrail records the IAM API call shortly after it happens.
CloudTrail stores log files at regular intervals in an S3 bucket. These logs are valuable for deeper investigation, compliance reporting, and audit purposes.
An EventBridge event is generated when the API call is logged by CloudTrail. An EventBridge rule captures relevant IAM events and triggers an associated target.
The EventBridge trigger invokes a Lambda function. This function processes the event, extracts key details, and composes a notification message for SNS.
The notification is sent to an SNS topic, which then distributes the message to all subscribed recipients — typically the cloud platform and security teams subscribed via their email addresses.
Recipients receive the notification and can take appropriate action based on the nature of the event, ensuring timely awareness and response to critical IAM activity within the AWS account.
Walkthrough
Step 1: Deploy Base Infrastructure
We’ll start by deploying the foundational infrastructure using Terraform. The complete code for this walkthrough is available on GitHub. You can either clone the repository or manually copy the code to your local environment. Inside the project directory, you’ll find multiple Terraform configuration files that define all the necessary resources.
Before deploying, you’ll need to update a key Terraform variable. Open the terraform.tfvars file — it contains the following parameters:
application_name = "cloudtrail-alerting"
iam_events = [
"DeleteUser",
"CreateUser",
"CreateGroup",
"DeleteGroup",
"CreateAccessKey",
"DeleteAccessKey",
"DeleteVirtualMFADevice",
"DeactivateMFADevice"
]
sns_endpoint = "[email protected]"
The important variable to update is ns_endpoint. Replace the placeholder with the email addresses where you’d like to receive the SNS notifications generated by this demo.
Once that’s done, initialize and deploy the infrastructure by running:
terraform init
terraform apply
These commands will initialize the required Terraform providers and provision the full infrastructure stack.
Step 2: Accept SNS Subscription
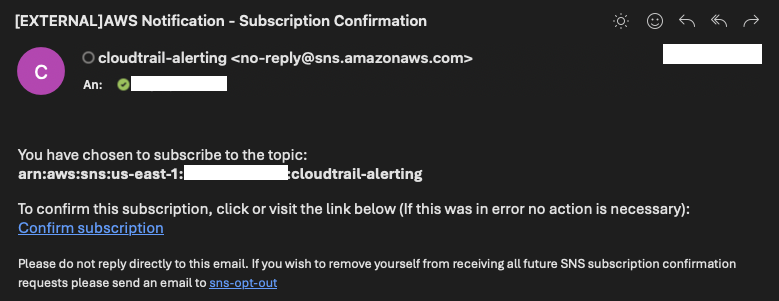
Once the infrastructure has been deployed, you should receive an email from cloudtrail-alerting [email protected] with the subject [EXTERNAL] AWS Notification - Subscription Confirmation.
To start receiving notifications from the SNS topic, you’ll need to confirm your subscription. Open the email and click the Confirm Subscription link. This will take you to a confirmation page indicating that your subscription has been successfully confirmed.
Step 3: Create IAM User
The next step is to test the setup by logging into the AWS Console and creating, then deleting, an IAM user. If everything has been configured correctly, CloudTrail should capture both the CreateUser and DeleteUser API calls, and you should receive notifications via SNS.
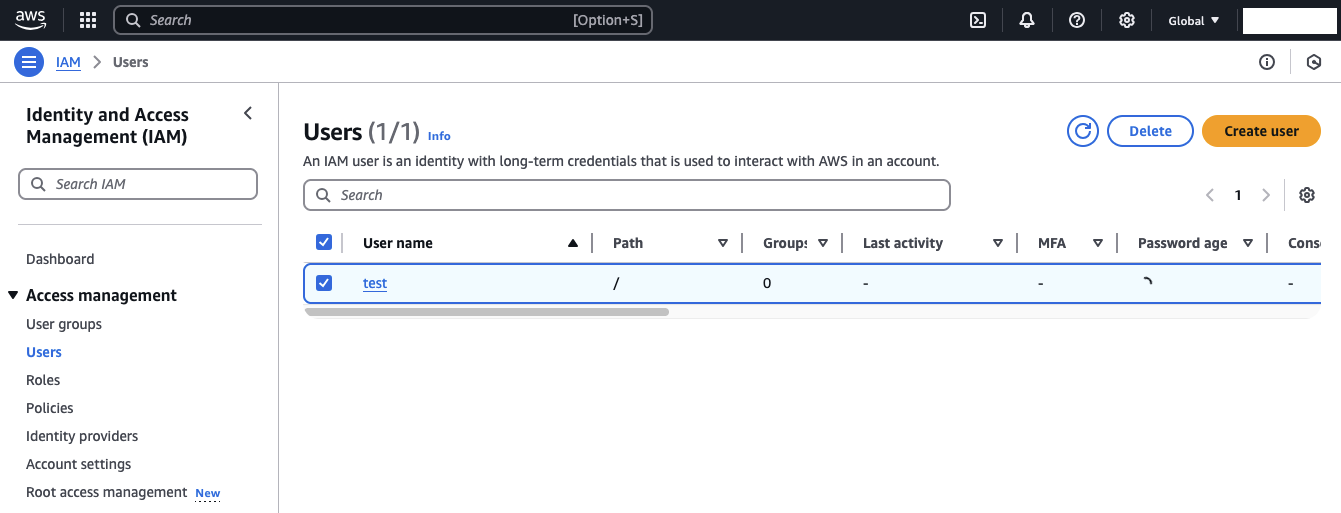
To begin, navigate to the IAM service in the AWS Console and select Users from the left-hand menu. Click Create user to start the user creation process.
Provide the user details. In this example, we’ll name the user test, grant them console access, and assign administrator permissions. After configuring the user settings, click Create user to finalize the creation. On the final screen, you can retrieve login credentials if console access was enabled.
Return to the IAM console, where you should now see the newly created user listed.
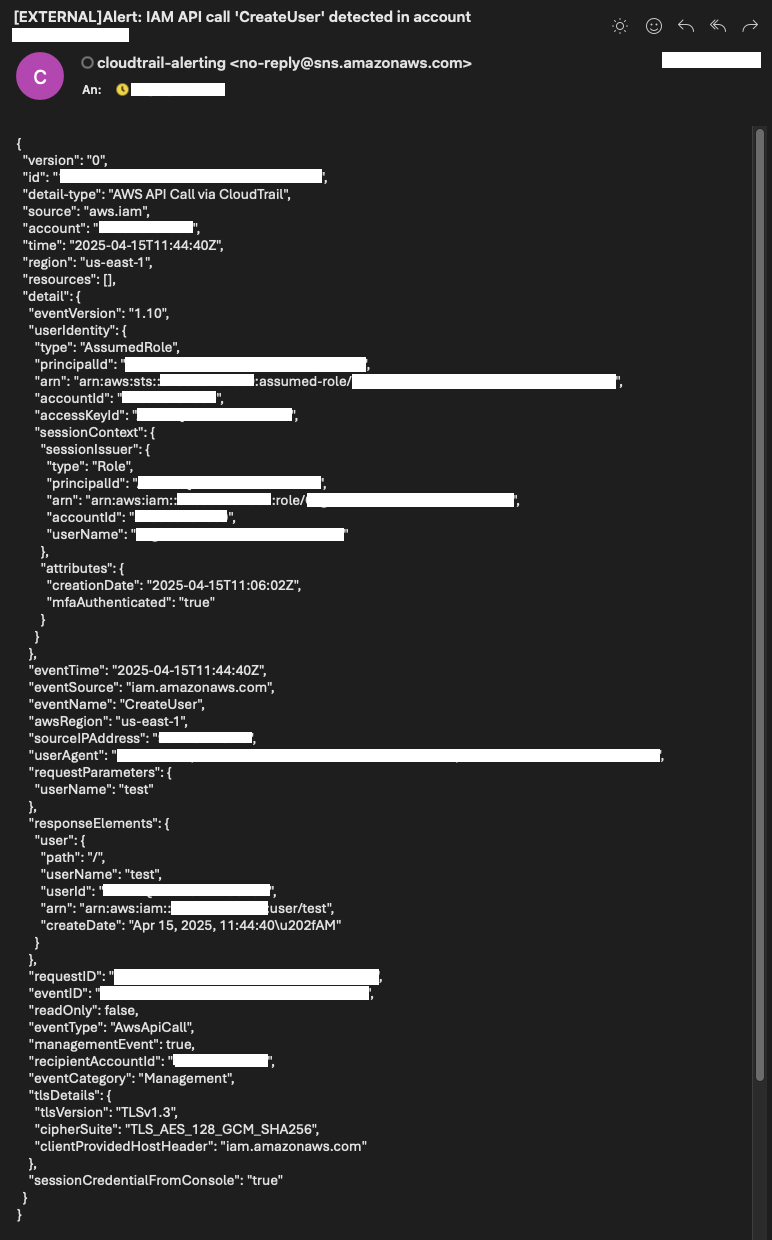
At the same time, you should receive a notification email from SNS alerting you to the IAM user creation event. The email subject will indicate the API action CreateUser along with the AWS account in which it occurred. The body of the message contains the complete event payload in JSON format, providing detailed context about the API call — including who initiated it, when it happened, and the specifics of the created user.
This allows administrators and security teams to quickly assess whether the activity is expected or potentially suspicious.
Step 4: Delete IAM User
After creating the IAM user, the next step is to delete it. This action should also trigger an event and send a corresponding notification through SNS.
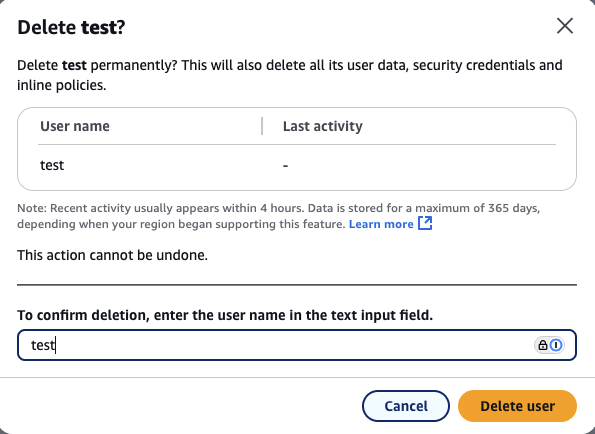
In the IAM console, select the newly created user and click Delete in the upper-right corner. To confirm the deletion, enter the username when prompted.
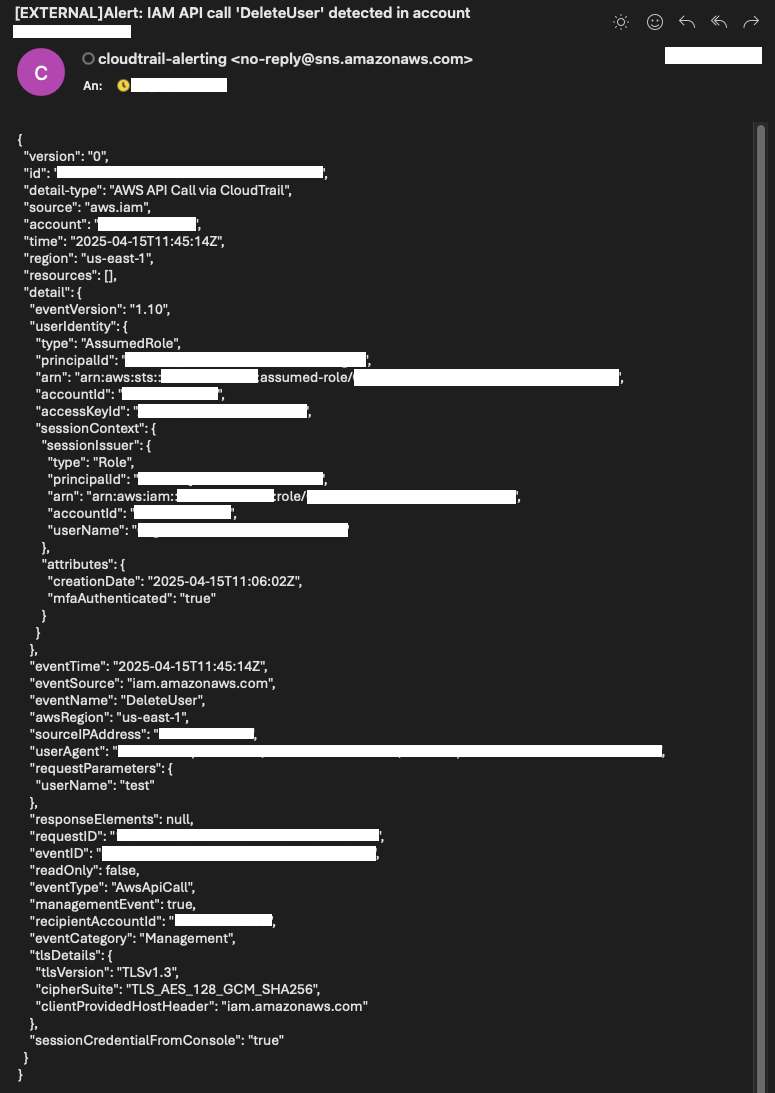
Once the user has been deleted, you should receive an SNS notification similar to the one from the user creation event. This time, the notification will indicate that a DeleteUser API call was made in your AWS account. As before, the body of the email contains the full event payload in JSON format, providing details about who initiated the deletion, when it occurred, and which user was removed.
This detailed event data makes it easy for administrators and security teams to quickly review and investigate the action if needed.
Congratulations — you’ve successfully built a notification pipeline for monitoring defined AWS IAM API calls!
Further Discussion
The two scenarios we covered — creating and deleting an IAM user — serve as examples of how this notification pipeline works. The demo also includes alerting for other important events, such as when the Root user is used within the account.
The specific API calls being monitored are defined in the Terraform variable iam_events, and you can easily customize this list to suit your needs. Feel free to add or remove API actions based on the activities you want to track in your environment.
Additionally, this simple demo can be extended and automated further. Instead of manually reviewing SNS email notifications, you could integrate event messages with a central log aggregation or security system, such as a SIEM, for automated processing, correlation, and response.
Use this demo as a starting point to build out a more robust monitoring and notification framework tailored to your AWS workloads.
Summary
In this blog, we explored how to monitor AWS IAM activity by combining CloudTrail, EventBridge, and SNS to build a real-time alerting pipeline for critical IAM API calls. By actively tracking actions like user creation, deletion, and permission changes, you gain immediate visibility into both intentional and accidental changes within your AWS environment. This setup helps improve security posture, maintain compliance, and reduce the risk of unauthorized access or privilege escalation, ensuring your cloud infrastructure remains secure and well-governed.
I hope you enjoyed this example and learned something new. I look forward to your feedback and questions. For the complete example code, please visit my Github.
— Hendrik


